What You Need to Know About Cyber Security Management
Table of Contents

Data drives the economy. It influences business decisions, from operations to sales and beyond, making it entrenched in everyday life. But with this uptick in data use comes risks, increasing the need for vulnerability management in cybersecurity. This is where a cybersecurity management plan comes in.
Cybersecurity management is now an integral part of organizations, as security risks threaten the structural integrity of operations. Managing cybersecurity risks involves all-around measures to protect an organization’s sensitive information.
In this blog, we will dive deep into the role of cybersecurity management in maintaining data safety, vulnerability management in cybersecurity and what steps to take to advance in the cybersecurity space. Read on to know more!
*semanticscholar.org
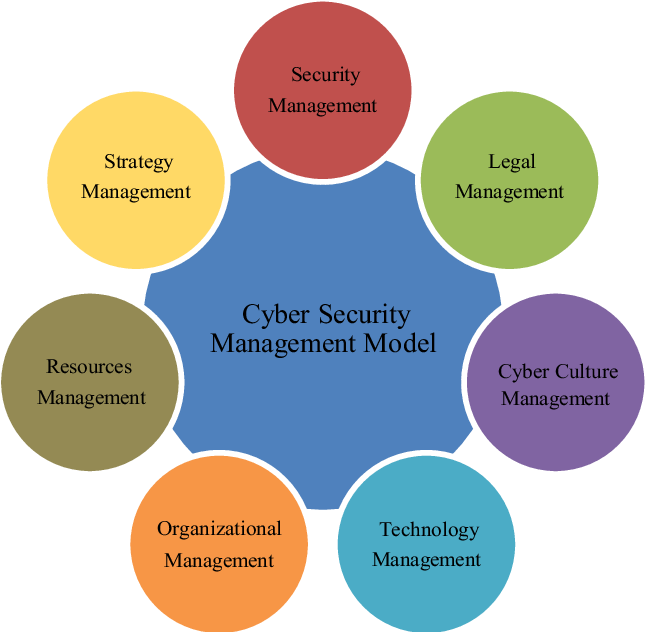
What is Cybersecurity Management?
Cybersecurity management is the concept of protecting a company’s data from cyber threats. There are many types of databases including:
- Networks
- Information Systems
- Internet of Things
- Digital Assets
Primarily, managing cybersecurity risks involves protecting these aspects of a company’s operations from unauthorized access and breaches from those who want to illegally gain access to an organization’s information. With threat management in cybersecurity, specialists can plan preventative and responsive measures to these problems so that the company’s sensitive information remains confidential.
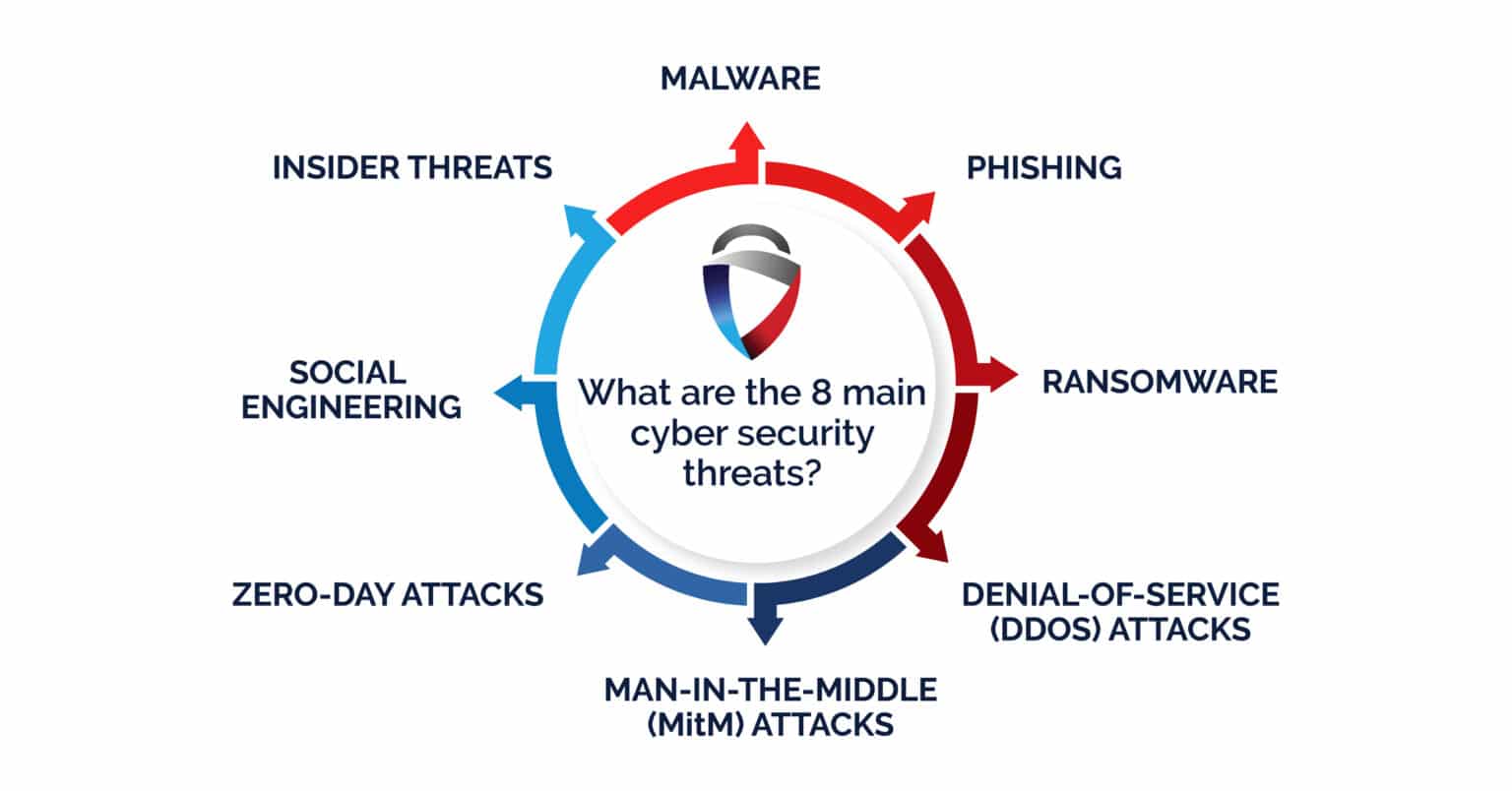
What are Cybersecurity Risks?
Organizations usually face some common cybersecurity attacks that compromise their digital assets. Here are a few you must know:
| Cybersecurity risk | How it affects data |
|---|---|
| Phishing | A fraudulent entity disguises its identity as a trustworthy professional and gets organizations or employees to share sensitive information. Then, they steal large amounts of data. |
| Malware | Malware is a malicious program that can be shared through hardware or online links. It can damage interconnected systems, corrupt data and delete digital assets. |
| Ransomware | Ransomware corrupts files by encrypting them and demands a ransom to decrypt them. |
| Denial of Service (DoS) | This cybersecurity threat disrupts regular operations by pushing false requests for products or services. |
| Wiping | Wiping is using malicious programming to completely delete all data from an organization’s system. |
*fortifydata.com
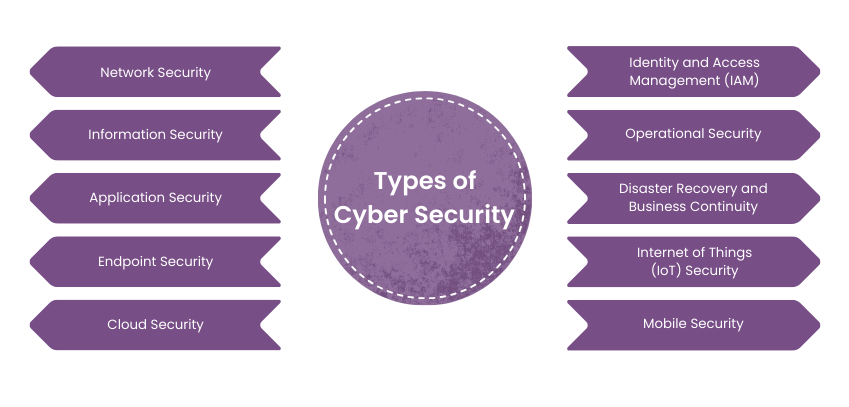
Types of Cybersecurity Management
Managing cybersecurity risks involves creating a robust, dynamic and comprehensive plan to ensure the structural integrity of the company’s data from any potential risks. Moreover, it also involves having a response in case a breach does happen. The most common cybersecurity management plans include:
1. Risk Assessment and Management:
Risk assessment is one of the most important strategies of cybersecurity management. It involves a team of cybersecurity specialists working together to test the current integrity of the databases internally. If they identify holes in the protection, then they work to fix these holes and make the protection stronger and more stringent. This is done in 4 steps.
- Maintaining a database of all the digital assets that could potentially be under threat.
- Understanding the different kinds of threats, also known as the Indicators of Compromise (IOC) and Indicators of Attack (IOA) and coming up with a cybersecurity management plan.
- Fixing issues internally so that external forces cannot breach the security line.
- Keeping an eye on the security measures and making sure they stay strong.
2. Data Monitoring:
Along with running continuous risk assessment strategies, cybersecurity management specialists also analyze data for threats in real time using Digital Risk Protection strategies. They monitor external threats and make sure that every aspect of their database, including on-site infrastructure, remote setups and cloud data are best protected. One of the key mechanisms for this is the Security Operations Centre or SOC. SOC detects threats with advanced technological tools like Intrusion Detection System platforms.
It also involves responding to threats with robust vulnerability management in cybersecurity measures. Data monitoring is done by cybersecurity specialists as well as AI and ML models that are trained to keep an eye out for security attacks.
3. Incident Response Strategies:
Every organization’s cybersecurity management plan involves a comprehensive strategy to deal with cybersecurity threats in case they manage to crack the protective wall.
| Steps of the Cybersecurity Management Plan | How it works |
|---|---|
| Identifying threats | What are the threats? Which part of the database is it affecting? |
| Delegating responsibilities | Which cybersecurity management team is responsible for this threat? How can they be notified immediately to manage cybersecurity risks? |
| Response plan | What level of security breach is this threat? How do we tackle this cybersecurity risk? What is the outcome of this response? |
From initial response to mitigating the risk and resolving it, an incident response plan is a key part of cybersecurity management. SOC helps here by investigating the data breach and providing an impact analysis report to understand the extent of the damage so steps can be taken to effectively reduce mistrust amongst consumers and stakeholders alike.
Answering all these questions helps organizations be ready for any attack. The overall point of having a plan in place is to not become complacent about cybersecurity threats, but rather, to be ready to spring into action and minimize the damage caused. Sometimes, cybersecurity threats are inevitable. However strict an organization’s protective measures are, a complicated problem might cause issues. So, a proactive incident response plan is integral.
4. Security Protocols:
Every organization has basic to advanced vulnerability management in cybersecurity in place to maintain everyday protection of sensitive information. Identity and Access Management is a key part of threat management in cybersecurity because it ensures that there is a step-by-step authorization process to access sensitive information in an organization’s database.
Identity and Access Management manages the employee roster and has a system in place to allow different levels of access to information depending on their position in the workplace. Mechanisms like password protection, two-factor authentication and biometrics are key in cybersecurity management. IAM is crucial in maintaining database confidentiality and integrity. This information centralization ensures that there is no unauthorized access to data while also combating threats from within the organization.
With increasing AI and ML use, high-quality technology can be trained as a part of managing cybersecurity risks. As the complexity of the threats increases, the sophistication of security protocols must also increase to keep up with the threats.
*theknowledgeacademy.com
Role of Cybersecurity Management in Organizations:
Cybersecurity management plays a key role in ensuring data protection and organizational integrity. When the reliance on data increases, organizations are also left vulnerable to cyber threats.
1. Protecting Organizational Data:
The main role of managing cybersecurity risks is to protect an organization’s data. This includes sensitive customer information, financial records and IP. Threat management in cybersecurity ensures that there is no unauthorized access or alterations to the data. Cybersecurity management involves:
- Complying with cybersecurity laws during operations
- Limit exposure to different employee groups with authorization levels
- Using technical protective measures like firewalls and encryption
- Establishing robust backup and recovery protocols to mitigate the impact of data loss from cyberattacks or system failures.
2. Preserving Organizational Integrity:
Every stakeholder, may it be a customer or an investor, trusts an organization with their sensitive information, financial data, etc. In the event of a security breach, the organization’s trustworthiness, reliability and ethics are affected. A single data breach can severely damage an organization’s reputation, eroding customer confidence and stakeholder trust. Cybersecurity management reduces the likelihood of such incidents by proactively identifying vulnerabilities and implementing preventive measures. The faster vulnerability management in cybersecurity is implemented, the sooner risks are mitigated, and businesses can carry on as usual.
3. Adapting to Competitive Business Environments:
As data continues to evolve dynamically, so will the sophistication and complexity of cyber threats. This is why cybersecurity management plans are critical as businesses grow and evolve. This way, they can stay ahead of the curve and establish themselves as the best player in the market. Periodic audits and vulnerability assessments enable organizations to identify weaknesses and address them promptly. For example, internal penetrative testing can help identify weaknesses in the security systems and fix them before external threats can occur. Ultimately, a strong culture of cybersecurity ensures that every employee understands the importance of data protection and takes responsibility for maintaining security protocols.
4. Fostering a Safer Work Culture:
Cybersecurity management leads to proactive risk management. It teaches organizations to be ready from the get-go to deal with internal and external threats. Cybersecurity management includes regular training programs to educate employees, regulate their access to data and prepare them to be careful while accessing it. Cybersecurity management is integral in the digital era, where data is the centre axle of operations, putting operational integrity constantly at risk.
In a nutshell, implementing robust security measures, fostering a safe and protected work culture and monitoring data to stay ahead of the threats ensures the protection of sensitive data and sustains organizational trust and credibility. By doing this, organizations can be safe now and, in the future, maintain their digital assets with the topmost security measures and ensure seamless operations.
Study Cybersecurity Management Facilitated through Jaro Education:
Whether you are already in the cybersecurity management industry or wish to shift gears and move careers, upskilling is key. This is possible through education, peer reviews, networking and mentorship, all of which are possible with the right certification courses. These certification courses deal with aspects like vulnerability management in cybersecurity, threat management in cybersecurity and more. Jaro Education aims to be the bridge that you need to connect to the best online cybersecurity management education from top universities in the country. We offer:
- Advanced, high-quality and expertly designed cybersecurity management certification courses from the best universities in the country.
- Free 1:1 mentorship with applications, career counselling, mock interviews and more.
- Access to AI-powered tools with which you can level up your cybersecurity management game and climb up the career ladder.
- You also have access to Jaro Connect, an exclusive alumni forum to network and build your connections in the industry.
- Free online pre-recorded resources from cybersecurity management experts in the industry.
Some certification courses in cybersecurity management include:
| University | Course |
|---|---|
| IIM Nagpur | PG Certificate Programme in Cybersecurity Management and Data Science |
| Amrita AHEAD | Online MCA Specialization in Cybersecurity |
Final Thoughts
Cybersecurity management is more than just managing and protecting data. It involves integral strategies to protect a company’s sensitive information, and by extension, its reputation and trustworthiness. Understanding how vulnerability management in cybersecurity works will keep organizations ahead of the curve and build a strong line of operations. A strong cybersecurity management specialist will be able to provide the right skill set to the organization to achieve this status.
Frequently Asked Questions
Cybersecurity management is the efforts taken by organizations to protect data from breaches, security risks and inconsistencies. It involves testing databases for gaps in protective measures and making barriers to entry stronger and more secure. Threat management in cybersecurity is one of the most important aspects of organizations dealing with large amounts of data.
Yes. Cybersecurity management is one of the most actively evolving and in-demand areas of the IT and technology sector. Well-rounded and skilled cybersecurity specialists are great assets to any organization. So, a degree in cybersecurity management will help you carve a niche in your career.
A cybersecurity management plan involves the 360-degree initiatives taken to protect sensitive data from security breaches. It has 4 steps including identifying, analyzing, addressing and preventing security issues. Managing cybersecurity risks requires stringent measures and solutions to keep phishing, hacking, etc. at bay.
Managing cybersecurity risks requires a multi-faceted plan that protects sensitive data from all directions. This primarily includes a dynamic incident response plan in case of a security breach. Moreover, the cybersecurity management team must also continuously monitor data privacy and perform cyber risk assessments to keep it safe. Strict security protocols like two-factor authentication, web application firewalls, etc., should also be implemented.
Cybersecurity management includes assessing risks such as phishing, hacking, data leaking, ransomware/malware and a DoS (Denial-of-Service) attack. Other risks like security breaches to the cloud or IoT could also threaten the integrity of your database. Vulnerability management in cybersecurity is key in these cases.