Integrating Data Privacy with Cybersecurity: Strategies and Tips
Table of Contents

- jaro education
- 11, January 2024
- 9:00 am
Denial of service and malware attacks are popular methods hackers seek to access various software. Effective testing and mandatory updates on software before and during IoT deployments leave several digital companies vulnerable to data privacy invasions.
For any online business, developing cybersecurity strategies to perfection is a cornerstone to ensuring personally identifiable information (PII) is safe to handle. This information is relevant to clients, website visitors and potential consumers.
Furthermore, Cybersecurity management is revamping the contemporary business ecosystem in this age of uncontrollable digital environment. The possibilities of cyber crimes and attacks are increasing to a great extent. Therefore, the experts must plan, prepare, manage and relieve the influx of cybersecurity risks.
Given this, you must think ahead and consider joining the PG Certificate Programme in Cyber Security Management and Data Science conducted by IIM Nagpur. This unique and comprehensive techno-managerial training module equips senior and middle management corporate profiles with adequate insights into cybersecurity management and reinforces their management credentials in the respective work domain.
The course, aims to rebuild tomorrow’s startups in turbulent times, leveraging the strength of cybersecurity management and developing cybersecurity strategies with artificial intelligence and data science. After completing the online sessions, participants are able to understand and tackle cybersecurity managerial communication and correspond decision-making along with practical and simulated multi-dimensional tool-based exposure using case studies.
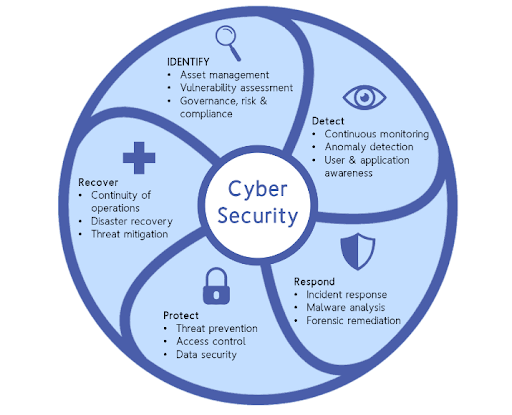
Interpretation of Cybersecurity and Data Privacy
Cybersecurity strategies involve protecting digital systems, programs and networks from prospective digital attacks. The domain is vast and embraces everything from threat recognition to incident response. Therefore, it demands a deep knowledge of all likely threats, such as malware and phishing attacks. These invasions usually aim to disrupt routine business operations and extort money from users. These security breaches may also access, modify or destroy sensitive information.
On the other hand, data privacy confirms that the acquired data and its usage by digital businesses are dealt with and preserved with optimum security according to the privacy rights of the users. This specific action involves the various available regulations that control data handling. These governing statutes include GDPR (General Data Protection Regulation) in Europe and CCPA (California Consumer Privacy Act) in the United States.
Besides, the NIST (National Institute of Standards and Technology) and the ISO (International Organisation of Standardisation) have also published guidelines on data privacy and cybersecurity strategies in their updated standards. The latest ISO 27701 releases amply provide instructions for cybersecurity measures. It is an extension of ISO 27701 and may become the basis of future GDPR certifications for the corporate world.
Apart from that, the elements of cybersecurity and data privacy are interconnected. You must implement a robust cybersecurity protection policy to ensure data privacy. On the other hand, corporate cybersecurity efforts will only be meaningful when committing to data privacy. This interdependence is a delicate balancing act that demands comprehensive and meaningful cybersecurity strategies and consistent supervision.
*eagleedge.com
Risks of Disregarding the Elements of Cybersecurity and Data Privacy
Ignoring the concepts of cybersecurity and data privacy can adversely impact contemporary businesses. Consistent data breaches can lead to substantial financial losses, damage brand identity, and loss of customer trust.
In a business sphere, where prospective consumers are progressively aware of their data usage, companies failing to prioritize data privacy and create proper cybersecurity strategies will no longer survive due to the fierce competition and long-term damage to their reputations.
Further, international regulatory bodies are imposing stern regulations on data protection. Any non-compliance to these directives may amount to hefty penalties. To elaborate, under GDPR, multinationals can attract fines of up to 4% of their gross annual turnover for violating data protection mandates. This significant rise in the cost of non-compliance makes data privacy and cybersecurity a monetary and moral compulsion.
The Assured Role of Cybersecurity in Data Protection
Cybersecurity in IoT is not merely about dealing with technological intricacies; it also affects an organization’s people and processes. Modern businesses need to have transparent policies and modes of operation for handling in-house data. Further, this data has to travel a clear line of communication and be understandable to all concerned employees. It includes all possible metrics, from password policies to methods to manage sensible data.
Moreover, modern business entities need to cultivate a culture of security wherein all stakeholders must realize the criticality of protecting data and developing cybersecurity strategies and commit to playing their part sincerely and efficiently.
Implementing Futuristic and Effective Cybersecurity and Data Privacy Measures
Integrating the most appropriate cybersecurity and data privacy strategies requires a multi-dimensional approach. The following are some valuable steps that businesses can take:
Risk Evaluation
You need to identify the existing data stored in your virtual repository, assign persons who will access it, and explore the risk elements involved. This action will enable you to understand the scope of your vulnerabilities and what checks you should apply. Periodical risk evaluation should be mandatory to refresh your cybersecurity strategies. This way, you will be free of any upcoming threats.
Data Depletion
Make sure you gather and store only the needed data. The optimum level of data bank will be a positive aspect of your business as it will be unnoticeable to cybercriminals. This policy is also a critical requirement of several stringent data protection regulations that stipulate companies must collect data for specific, logical and legitimate purposes.
Adequate Security Measures
Also, it will help if you implement strong security measures. These steps include the installation of firewalls, data encryption, and multi-factor authentication. You must regularly patch and update your operational systems to prevent potential threats. Tracking and monitoring the systems for any abnormal activity is also necessary. Early detection of threats and malware can appreciably reduce the chances of data breaches.
Staff Training
The management of the companies should arrange training sessions concerning data privacy and cybersecurity and educate them on best practices. The courses should cover everything from identifying phishing emails to protecting client data. Regular structured training will guarantee data security will always be a focal point in the minds of the organization’s employees.
A postgraduate program on Cybersecurity Management and Data Science under the aegis of IIM Nagpur is an ideal option for candidates pursuing a certificate course to initiate their remarkable growth in the respective field. Eminent MNCs may sponsor their personnel to participate in this valuable program.
Incident Response Proposition
There must be a proven action plan for promptly responding to a data breach or cyberattack. It should include developing cybersecurity strategies for suppressing the incident, analyzing the damage inflicted, informing the affected stakeholders and swiftly recovering from the occurrence. A meticulous plan and effective execution can alleviate the impact of the cybersecurity breach and assist in restoring customers’ trust.
The Future Roadmap of Cybersecurity and Data Privacy
Any company management and the respective CXO always anticipate future happenings. They presume that the landscape of data privacy and cybersecurity will continue to evolve with the intense handling of voluminous data. The fast-paced technological headway brings fresh opportunities for digital businesses. In hindsight, it also brings new challenges in complex cyber threats.
The unique features of AI (artificial intelligence) and ML (machine learning) have contributed to an extensive application of cybersecurity measures. These preventive measures offer a proactive intent to threat detection and subsequent response. They are as follows:
Advanced Threat Diagnosis
The high-end AI and ML algorithms can analyze a significant quantity of data points at an unbelievable scale and velocity, which is beyond human capacity. They can recognize patterns and deviations that enable early detection of future cyber attacks and curtail response time. For instance, AI can detect abnormal website traffic, leading to data privacy violations. It may also identify sceptical user behavior that might signal a possible phishing attack.
Highly Automated Incident Response
You can automate incident response requirements through AI applications. It helps companies to respond promptly and efficiently to cyber incidents. AI-driven platforms can effectively assess and correlate security events, establish requisite alerts and take remedial actions.
Super Intelligent Authentication
Advanced and sophisticated AI algorithms can accurately confirm user identities, minimizing the risk of unauthorized cyber access. Besides, AI-powered authentication arrangements can adjust to evolving data privacy threats and dynamically restyle prevailing security checks as per risk levels.
Privacy Safeguarding Techniques
The principles of AI can immensely contribute to data privacy by adopting privacy-preserving techniques. Federated learning, differential privacy and homomorphic encryptions are ideal instances of AI-driven perspectives that assist companies in analyzing data without compromising independent privacy.
Conclusion
The message is loud and clear for global business leaders, i.e. to embrace a holistic path that integrates data privacy and cybersecurity. If they follow these steps, they can protect their organization’s most valuable intangible assets. In this way, they also strengthen the company’s stability against the ever-escalating landscape of cyber threats.
These days, the demand for hybrid techno-management professionals has got more attention and the PG Certificate Programme in Cyber Security Management and Data Science organised by IIM Nagpur is the perfect forum to begin your journey to become a cybersecurity expert. This distinct program caters to the requirements of mid-management professionals, CXO and CTO level executives. So, if you are one of them, then you must definitely go for it.
The course commences in three phases: cyber security, risk assessment and management. Aside from technical skills, it recapitulates elements like communication, strategy, leadership, team management and control, and the core ideas of holistic cybersecurity approaches in a fast-changing landscape. If you are a graduate with at least three years of work experience, you can enroll in the program through Jaro Education.










1 thought on “Integrating Data Privacy with Cybersecurity: Strategies and Tips”
Great insights on the importance of integrating data privacy with cybersecurity! This blog highlights crucial strategies for protecting sensitive information.