Identity Access Management (IAM): Concepts

Table Of Content
- Why is IAM important?
- Components of IAM
- IAM Tools
- IAM Benefits
Why is IAM important?

Components of IAM
IAM Tools
IAM Benefits
In the area of security, using an IAM set can make it easier to enforce user authentication, validation and permission regulations. Furthermore, it helps to solve concerns about power creep. With the use of IAM, people and services are appropriately verified, authorised and audited, and access rights are provided in accordance with policies. Implementing identity access management systems enables firms to function more efficiently by reducing the time, effort, and money necessary to manage network access manually. IAM systems help businesses better comply with regulatory rules by demonstrating that they are not exploiting company information. Companies can also show that any data required for audits is readily available. Companies that handle identities effectively have better control over user access, lowering the chance of internal and external data breaches.
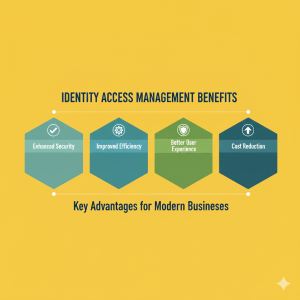
Implementing IAM solutions and adhering to the best practices can help businesses obtain a competitive advantage. IAM solutions enable businesses to grant individuals outside the organisation, like partners, suppliers, contractors and customers, access to their network. They can provide access via on-premise applications, mobile applications, and SaaS without jeopardising security, which in turn will improve cooperation, lead to higher production, increase efficiency, and lower operational expenses. Many developing IAM solutions aim to decrease risk by keeping personally identifiable information with the owner of the information rather than distributing it across susceptible databases.
A decentralised identity system, for example, allows individuals to keep control over and manage their own identities. Individuals may control how and where their personal information is shared, potentially lowering company risk and responsibility. Thus, IAM is centred around managing the digital identities of individuals, like employees, partners, and customers. They can control their access to systems, applications, and data based on their roles, responsibilities, and permissions. By implementing IAM solutions, organisations can mitigate the risks associated with unauthorised access, data breaches, and insider threats.
IAM Best Practices
IAM Challenges & How to Overcome Them
Get Ahead in Cybersecurity with the Executive Programme in AI & Cybersecurity For Organizations by IIM Indore
To enhance your cyber security knowledge, apply for the 10-month Executive Programme in Cyber Security for Organizations [EPCSO]. This course is brought to you by the prestigious IIM Indore. It has a holistic curriculum enabling interactive online learning. You can indulge in capstone projects that will give you an overall career enhancement to be ready for professional complexities.
Frequently Asked Questions
Find a Program made just for YOU
We'll help you find the right fit for your solution. Let's get you connected with the perfect solution.

Is Your Upskilling Effort worth it?
Are Your Skills Meeting Job Demands?
Experience Lifelong Learning and Connect with Like-minded Professionals

