Digital Forensics Tools and Techniques in 2025
Table of Contents

- jaro Education
- 18, July 2023
- 4:00 pm
In the modern context, forensics software remains a critical component that allows specialists to reveal hidden data, retrieve important information, preserve integrity, anticipate files, and examine fine details. These all become important in sustaining the integrity of evidence in court. Digital forensic tools are critical for law enforcement agencies and incident response capacity building, but they have also become essential for the success of cybersecurity professionals and maintenance programs across many sectors.
Why does it matter?
- Over 90% of modern crimes always leave a digital trail.
- A global cost of cybercrime that exceeds 8 trillion dollars by 2025 (Source: Cybersecurity depends on Ventures).
- 85% of organizations suffer at least one incident of digital security every year (IBM Security Report).
Understanding the Digital Forensics Tools
Digital forensics tools involve identifying, acquiring, and analyzing electronic evidence, which plays a crucial role in modern criminal investigations. It is used in courts and helps in scrutinizing cyberattacks and responding to incidents. Gathering electronic evidence from various sources, like computer forensic tools, mobile devices, and more, is a key aspect of digital forensics.
The Broad Impact of Digital Forensics
Digital forensics tools extend beyond computer forensics and have a significant societal impact. In today’s connected world, digital evidence plays a crucial role in solving crimes and legal matters in both the digital and physical worlds.
Connected devices generate vast amounts of data, logging user actions and autonomous activities. This includes various devices like cars, mobile phones, routers, and even traffic lights.
Digital forensics is essential in:
- Investigating data theft and network breaches
- Understanding online fraud and identity theft
- Gathering evidence for violent crimes
- Identifying and prosecuting white-collar crimes.
Within organizations, digital forensics tools aid in cybersecurity and physical security incidents. It enables incident response, threat detection, root cause analysis, and threat eradication, which provides evidence for legal teams and authorities.
Digital Forensics Tools
Digital forensics tools are computer forensics software applications or hardware devices specifically designed to aid in the investigation and analysis of digital evidence. These tools assist digital forensic examiners in tasks such as data acquisition, data recovery, data analysis, and reporting. Common digital forensics tools include:
1. Sleuth Kit (TSK)

*SalvationDATA
The Sleuth Kit (TSK) is the most advanced and open-source toolkit for computer forensics investigations into disk images and file systems, along with their recovery. It is becoming the first choice for digital forensics tools practitioners and incident responders.
Key Features:
- File System: NTFS, FAT12/16/32, exFAT, UFS1/2, Ext2/3/4, HFS+, etc.
- Disk Imaging: Raw Disk Images, EWF (Expert Witness Format), and AFF.
- Metadata Extraction: View timestamps, deleted files, and other file system metadata.
Command-Line Tools: Some of the following utilities are available:
- fls – List files and directories
- . icat – Extract file content by inode number
- . fsstat – Shows file system stats.
- mmls – Displays the partition layout.
- tsk_recover – Recover deleted files.
Integration: Used along with other common tools such as Autopsy, which is a GUI front-end for making TSK accessible.
PROS
- File System Support: This forensic tool supports a whole range of file systems, allowing users to easily use it on various platforms.
- Community and Research Opportunities: Being open, it provides an excellent ground of study for researchers; this has also built a strong community around it.
- Integration with Autopsy: For the GUI experience, it could further be used along with Autopsy for better usability of computer forensics software tools
CONS
- Complexity
- Limited GUI Option
2. Autopsy

*Medium
Autopsy is a modular and user-friendly digital forensics tool platform that is used by investigators to assess data. It offers timeline analysis, harsh filtering, keyword search, web artifact extraction, file recovery, and rapid identification of indicators of compromise. Background jobs run in parallel, providing quick results for targeted keywords. It is currently available for Windows only for computer forensics software tools.
PROS
- Wide-ranging analysis, from file filtering to registry analysis, Autopsy is indeed a flexible tool, applying itself across a wide spectrum of investigations.
- Community Development: Open-source projects benefit from widespread use and contribution, meaning they would experience steady development.
- Educational Resource: With so many features and no price tag, it really turns out to be the first choice in classrooms.
CONS
- Performance Problems: It became a bit slow while processing larger datasets, reducing efficiency.
- Limited Support: Though very much community support is available, official support may not be available for complex queries.
3. Digital Forensics Framework

*ToolWar
Digital Forensics Tools Framework is indeed a free, open-source utility that is modular and extensible, designed to help both professional and novice users with the collection, analysis, and preservation of digital evidence of computer forensics software tools.
Core Functionalities
- GUIs and CLIs: You can use DFF in a typical GUI for convenience or be a total terminal ninja using the command line.
- Cross-platform: Of course, it runs on Linux, Windows, and Mac.
- Automation: Quite simply, it has Python scripting capabilities for the purpose of implementing automated workflows or for creating custom analysis scripts.
- Filesystem and artifact analysis:
- FAT, NTFS, HFS, Ext, etc., analyzing files, metadata, directories, and partitions. memory dump, disk image, and removable media.
4. X-Ways Forensics

*CDFS
It is a highly designed computer forensic tool for forensic examiners. It is renowned for its speed and low resource consumption. Built on the WinHex hex and disk editor, X-Ways Forensics tools
Provide a range of advanced features, including disk and data capture, computer forensics software tools, cloning, imaging, and various other tools. It offers a comprehensive solution for digital forensic investigations.
PROS
- Analysis Versatility Tools: Its analysis features, from file structure to data recovery, have a broad spectrum of capabilities.
- Flexible File System Support: It is a computer forensics software tool that has multi-file support for application handling.
- Updates are regular. It is updated regularly to keep in touch with what the industry is currently developing.
CONS
- Interface Troubles: The interface is a bit sophisticated, especially for those individuals who are not very familiar with digital forensics tools.
- Training Requirement: To a high extent, training must be given to tap its potential fully.
5. FTK
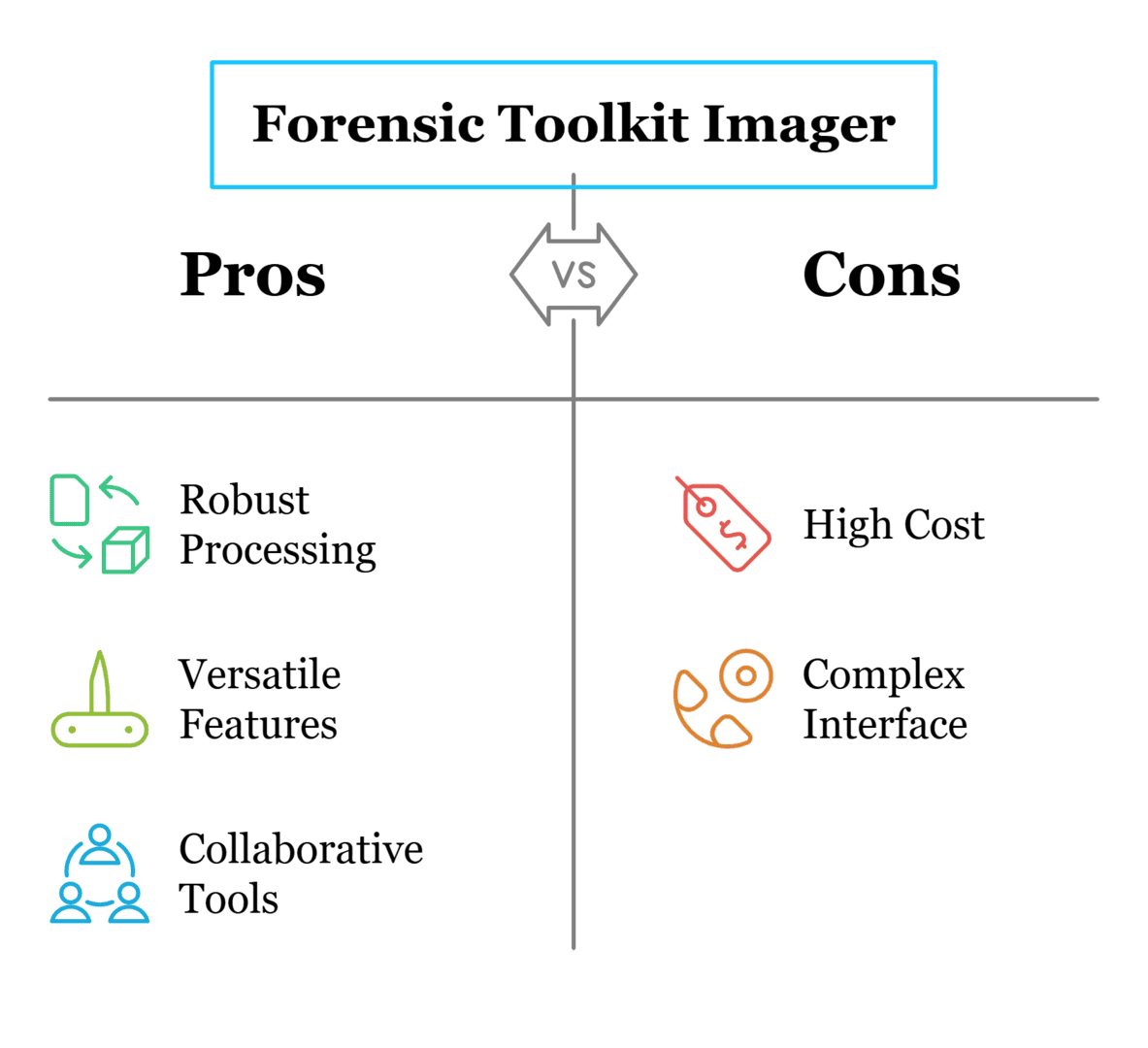
FTK Imager, a free forensic tool, ensures the integrity of digital evidence by analyzing drive images without modifying their original state. It supports all operating systems, recovers deleted files, parses XFS files, and generates file hashes for data integrity checks. Therefore, it is a crucial tool for forensic analysis
investigations.
6. Open Computer Forensics Architecture
It is an open-source framework for computer forensic tools, designed for digital media analysis within the environments of a digital forensics laboratory, and was initiated by the Dutch police.
OCFA runs as a backend for the Linux platform, where it can make use of a PostgreSQL database for datastores as well as custom content addressable stores or CarvFS-based datastores, along with Lucene indexes. Because of licensing issues, the OCFA front end is not open to the public.
The framework further integrates into other open-source forensic tools and comes with modules for the TKS, Scalpel, libmagic, Photorec, GNU Privacy Guard, EXIF tags, objdump, zip, 7-zip, gzip, bzip2, tar, rar, antiword, mbx2mbox, and qemu-img. OCFA extensibility towards C++ or Java.
7. SANS Investigative Forensics Toolkit
SANS Investigative Forensics Toolkit (SIFT) is a group of open-source forensics tools
and incident response technologies for deep investigations of various digital environments. Secure read-only imaging of the original disk, file types, etc., under secure conditions, is undertaken, preserving the integrity of evidence found.
Offering maximum flexibility regarding raw evidence formats, E01 (Expert Witness format), and AFF (Advanced Forensics format), SIFT is focused on the Ubuntu platform and contains several individual tools (some of which are listed here) that are free for forensic practitioners to use. And SIFT gets updated regularly.
8. EnCase

*ForensicStore
EnCase is a popular commercial digital forensics tool that offers comprehensive capabilities for data acquisition, analysis, and reporting. It offers a comprehensive computer forensics software tools package, from triage to final reports, streamlining the investigative process.
The recipient of SC Magazine’s “Best Computer Forensic Solution” award for ten years in a row is a renowned computer forensics software tool used in forensic cybersecurity investigations. Since 1998, EnCase has been instrumental in recovering evidence and analyzing files on hard drives and mobile phones, assisting professionals in criminal investigation cases.
9. Cellebrite UFED
Founded in Israel in 1999, Cellebrite specializes in mobile device forensics tools for law enforcement and enterprises. Their expertise lies in collecting, reviewing, analyzing, and managing data from mobile devices. The Digital Intelligence Investigative Platform offered by Cellebrite facilitates the unification of the investigative life cycle and the preservation of digital evidence.
10. Volatility

*Medium
It is a popular open-source memory forensics tool used for analyzing volatile memory dumps to extract valuable information.
Their open-source framework enables incident response and malware detection through volatile memory forensics, preserving crucial evidence during system shutdowns. Written in Python and compatible with various machines, it analyzes cached sectors, crash dumps, DLLs, network connections, process lists, and registry files. The tool is freely available, with its code hosted on GitHub.
PROS
- Plug-in Structures: You can create an analysis tailored to your needs.
- Plenty of Community Support: The community provides extensive documentation and support.
- Free: This tool is open-source and hence, accessible to anyone for free.
CONS
- Technical Know-How Needed: It requires a fairly good understanding of memory structures.
- Limited Official Support: Community support is strong, but official support may be limited.
11. Wireshark
Wireshark is the world’s most-used network protocol analysis tool, trusted by governments, corporations, and academic institutions worldwide. It provides microscopic-level visibility into network activity by capturing and analyzing network traffic. With a user-friendly interface available on multiple operating systems, Wireshark aids in detecting and investigating malicious activity. It supports various data sources and allows exporting of output in multiple formats.
12. Exterro
Founded in 2004 in Portland, Oregon, Exterro specializes in workflow-driven computer forensics software tools and governance, risk, and compliance (GRC) solutions. With a focus on assisting in-house legal teams, streamlining compliance processes, and managing risks, Exterro offers a range of products covering e-discovery, privacy, risk management, and digital forensics. Notably, their forensics-focused tools include capabilities for remote endpoint collection, scalable data processing, automated processes, and Mac and mobile data inquiries.
List of Most Powerful Digital Forensic Techniques
1. Digital Forensic Techniques
Digital forensics employs various techniques and tools to examine compromised devices. These techniques aid in uncovering hidden information, analyzing digital activity, detecting anomalies, and recovering deleted files. Here are some common techniques utilized in digital forensics.
2. Reverse Steganography
This involves uncovering hidden data within files by analyzing data hashing, which reveals changes in the underlying data structure.
3. Stochastic Forensics
It helps in investigating digital activity without digital artifacts, which is particularly useful for detecting insider threats and data breaches.
4. Cross-Drive Analysis
Professionals use this technique for correlating information across multiple drives to establish baselines and identify suspicious events.
5. Live Analysis
Live analysis helps in examining volatile data stored in RAM or cache while the device is running, typically conducted in a forensic lab to preserve evidence.
6. Deleted File Recovery
Recovering partially deleted files by searching for fragments spread across the system and memory.
These techniques play a crucial role in digital forensic investigations, providing insights into hidden information and reconstructing digital activities.
What Should One Consider in Choosing the Best Software for Digital Forensics?
1. Parameters for Law Enforcement, Commercial Organizations, and Incident Response
Specific Needs of Different Industries: In law enforcement, compliance becomes the highest order of priority and becomes significant in evidence preservation. Data should be an insatiable need as far as efficiency is concerned in the commercial world, with incident response teams required to quickly find and fix vulnerabilities. Understanding the requisite unique features adequately will only help in selecting the right digital forensics and computer forensics software tools that coincide with company goals and regulatory standards.
2. Scope: Individual Tools Vs. Suite of Tools
It’s your choice to choose from among a suite of tools or opt to buy them separately, depending on the jobs you want to accomplish. Individual programs can achieve every thing but a lot of the time it is easier and faster to string together several programs. A forensics software suite, on the other hand, is broader and can address several issues at the same time, thus making the process faster and easier during an investigation.
3. Concerns about Privacy or Security
His primary confidentiality and security control means that most would keep the digitized material under examination. The selected digital forensics software should also prevent any subsequent unauthorized access to the data during equipment review. Always check for defensive features like encryption, authentication, and write protection that provide an extra degree of protection for the tool. Before making a purchase, ensure that the product has been thoroughly checked for safety shortcomings and conforms to all the standards and regulations.
4. Open Source vs. Proprietary Tools: Expertise vs. User-Friendly
Although far more complicated and technical will most times be the understanding and practice required to maintain and update an open-source application, it will pay back that investment by being more flexible and tailored. Many proprietary systems, however, have intuitive interfaces and even provide one-on-one support to train users quickly to get started. Thus, many considerations would go into such a decision: what the team’s technical skill level is, whether any specific abilities are needed, and an openness to free or paid support.
5. Costing: Open-Source Tools, Basic Suites, Large Organizations
The choice of tools depends largely on the available budget. While it is more often than not the case that open-source programs are free, one never finds using them effectively without considerable knowledge on the part of the user. Suites that have just the very basic features could often be cost-prohibitive for all but the smallest businesses. Businesses of some size could afford more advanced and featured suites with helpful extras for support. Cost, functionality, and return on investment are all factors to consider while determining the right tool.
Choosing the best digital forensics software requires careful evaluation of a number of factors. Matching the tool with business aims, security standards, user experience, and budget ensures efficient digital investigations and reliability in processes.
Executive Programme in Artificial Intelligence and Cyber Security for Organizations [EPAI&CSO] IIM Indore
It aims at non-technical professionals and engineers, project managers in IT, and early-career IT professionals who are keen on acquiring knowledge for preventing and addressing cyber threats. This program confers on participants indispensable competencies in AI, digital transformation, and cybersecurity, thus making it ideal for career switchers and ladder climbers.
The curriculum pertains to fundamental AI concepts, machine learning, analytics generated by big data, visualization of data (Power BI, Tableau), generative AI, and technological novelties like blockchain and quantum computing, among others. It thus delves further into cybersecurity, including risk management, threat mitigation, incident response, digital forensics, and compliance with global regulations.
This program, which focuses primarily on leadership and communication, prepares one to ride on the innovations brought about by AI and the changing cybersecurity landscape.
Program Highlight:
Jaro Education: Learning Without Limits
Career and Support Counseling
In addition to being one of the leading online higher education providers, Jaro Education offers its complete academic program along with career guidance and support counseling. Education is just one part of the growth toward human productivity; therefore, Jaro emphasizes the same on how to translate knowledge into professional success.
Personalized Career Guidance
This counseling service of Jaro intends to help working professionals, fresh graduates, and executive learners, all of whom go through career goal identification and planning the most suitable educational and professional strategies to achieve them. Counselors enable students to:
- Understand strengths and areas for development
- Draft short- and long-term career goals
- Employ industry-relevant programs
- Facilitate transitions into roles or up-skilling
Dedicated Student Support
All through enrollment and after completing the program, Jaro’s support teams will handle a one-on-one approach with students. This includes:
- Academic Advisors follow students’ progress through course completion
- Career Counselors conduct resume reviews and interview tips while providing market insights
- Technical Support to assist in ensuring a seamless digital learning experience
Bottom Line
Digital forensics tools and techniques play a crucial role in modern investigations, allowing experts to analyze electronic evidence and uncover vital information. As technology continues to evolve, these tools become increasingly essential in solving crimes, detecting cyber threats, and preserving evidence for legal proceedings.
Every aspect of this program is designed to meet the specific needs of organizations. It offers a holistic curriculum through interactive online learning and capstone projects to enhance knowledge and skills in cybersecurity.
By completing this program, participants not only gain the prestigious alumni status of IIM Indore but also receive a certificate of completion. The program combines a three-day on-campus module with interactive online learning, culminating in a capstone project. If you are looking to excel in the field of digital forensics and cybersecurity by enhancing your professional capabilities and staying ahead in this rapidly evolving field.
Frequently Asked Questions
Computer forensic tools are software programs used to identify, preserve, analyze, and present digital evidence found on computers, hard drives, and other digital storage devices. They are essential in cybercrime investigations, legal proceedings, and corporate incident response.
Some widely used tools include:
- The Sleuth Kit (TSK) – CLI-based disk and file system analysis
- Autopsy – GUI frontend for TSK
- FTK (Forensic Toolkit) – Full-featured commercial suite
- EnCase Forensic – Industry-standard for legal-grade investigations
- X-Ways Forensics – Lightweight but powerful forensic analysis
- Volatility – Memory forensics
- KAPE – Triage and artifact collection
- Deleted files and folders
- Email messages and attachments
- Web history and downloads
- System logs and user activity
- Metadata (timestamps, file properties)
- Registry entries and artifacts
- Memory (RAM) contents
- Encrypted or hidden data
Yes! Some popular open-source tools include:
- The Sleuth Kit
- Autopsy
- Volatility
- CAINE Linux (a distro with multiple tools)
- Scalpel and Foremost (file carving)
- Bulk Extractor (keyword and pattern scanning)
- GUI tools (like Autopsy or FTK) offer user-friendly interfaces, ideal for beginners and quick visual investigations.
- CLI tools (like TSK or Volatility) offer more control, automation potential, and flexibility, but require command-line knowledge.










6 thoughts on “Digital Forensics Tools and Techniques in 2025”
Informative guide on digital forensics tools and techniques. Valuable resource for understanding investigative processes. Well-explained!
Thank you for your positive feedback on our digital forensics guide! Visit our site for more detailed information.
Fantastic post! The detailed breakdown of digital forensics tools and techniques is incredibly informative. Thanks for sharing this valuable resource!
We’re glad you found the post informative! Visit our site for more insights.
Informative article on digital forensics! The detailed breakdown of tools and techniques provides valuable insights into this critical field.
Excellent overview of digital forensics tools and techniques! The article provides valuable insights into essential methods for effective cyber investigations.