Understanding the use of Malware Analysis in Ethical Hacking

Table Of Content
- What is Malware Analysis?
- Types of Malware
- Malware Analysis Techniques
- Malware Traffic Analysis
What is Malware Analysis?
Malware analysis is the process of examining malicious software, or malware, to learn how it works, how it behaves, and what impact it may have. Malware analysis entails dissecting the malware and revealing its inner workings, such as identifying how it infects systems, its command and control mechanisms, and its intended goals. The primary goal of malware analysis is to comprehend the threat’s nature and devise effective countermeasures to reduce the malware’s impact. Malware analysis is an important skill for cybersecurity professionals, particularly ethical hackers and incident responders, because it allows them to identify and neutralise security threats while protecting systems and data from cyber-attacks.
Types of Malware
There are various types of malware, which are as follows:
- Virus
- Worms
- Trojan horses
- Ransomware
- Spyware
- Adware
Malware Analysis Techniques
Malware analysis assists cybersecurity professionals in gaining insight into how malicious programs work and spread. Through the use of different malware analysis methods, professionals can effectively identify, block, and contain potential threats.
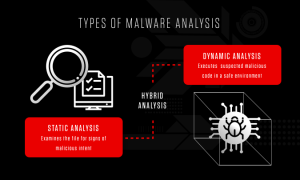
Malware Traffic Analysis
Malware traffic analysis involves examining network traffic to find, understand, and respond to harmful activities. It enables cybersecurity experts to spot communication between infected devices and command-and-control servers. By analyzing malware traffic, analysts can reveal attack patterns, methods for stealing data, and possible weaknesses in a network. This proactive method improves network security and aids in effective malware detection and prevention.

Key aspects of malware traffic analysis:
– Identifying unusual outbound and inbound network traffic.
– Detecting communication with suspicious IPs or domains.
– Analyzing packet captures (PCAPs) for harmful payloads.
– Using malware analysis tools like Wireshark and Zeek for detailed inspection.
– Correlating traffic behavior with known malware signatures and threat intelligence.
Dynamic Analysis
Purpose of Malware Analysis in Ethical Hacking
Malware Analysis Tools
Advanced Professional Certification Programme in Cybersecurity and Ethical Hacking
Combat cyber heists and eliminate security risks. Learn to prevent organisations’ cybersecurity mesh by developing security architecture with India’s top IIT to upskill and transform into well-suited and skilled Cyber Security Experts. Uncover key concepts in cybersecurity, ethical hacking, and their applications to reimagine organisational goals. Investigate IIT’s cutting-edge curriculum, combining theory and capstone projects, case-based learning, and more. Join the Advanced Professional Certification Programme in Cybersecurity and Ethical Hacking by E&ICT, IIT Guwahati, to advance your cybersecurity career.
Conclusion
Finally, malware analysis is an important skill in ethical hacking because it allows analysts to gain insight into the inner workings of malicious software. Ethical hackers can detect patterns and trends in the threat landscape by analysing malware, identifying vulnerabilities and attack vectors, and developing effective defence strategies to protect systems and data from cyber-attacks. Malware analysis tools and techniques assist ethical hackers in understanding the behaviour of malicious code and identifying and mitigating potential security threats. The importance of malware analysis in ethical hacking will only grow as cyber-attacks become more sophisticated. Ethical hackers can help to ensure security and safety by staying up to date on the latest malware analysis techniques and tools.
Frequently Asked Questions
Malware analysis is the process of examining malicious software to understand how it works, where it comes from, and what impact it has. With the help of malware analysis tools, experts can effectively detect, prevent, and reduce potential cyber threats.
There are three types of malware analysis: static, dynamic, and hybrid analysis. Each method, supported by malware analysis tools and malware traffic analysis, helps identify how malware behaves and communicates.
In ethical hacking, malware analysis is used to study and simulate malware attacks to improve system defenses. Professionals also carry out malware traffic analysis to monitor and block harmful communications.
The four main types of malware are viruses, worms, trojans, and ransomware. By using malware analysis and malware traffic analysis, experts can find and remove these threats with specialized malware analysis tools.
Find a Program made just for YOU
We'll help you find the right fit for your solution. Let's get you connected with the perfect solution.

Is Your Upskilling Effort worth it?
Are Your Skills Meeting Job Demands?
Experience Lifelong Learning and Connect with Like-minded Professionals

